-

The revised and compressed OWASP Top 3 Web Application Vulnerabilities
I love Top 10s. They’re everywhere and about everything: Top 10 Fascinating Facts About Neanderthals, Top 10 Crazy Bridal Preparation Customs, Top 10 Alleged Battles Between Humans And Aliens, etc. But my question was always: why 10? Why not 11? Or 9. Or whatever else? I guess 10 sounds more important than 11 or 9. It’s the decimal system, 10…
-

Short URLs are Harmful for Cloud Data Sharing
I was never a big fan of sharing cloud data through a unique link, rather than nominating the specific people that can access the data. To me it feels like security through obscurity. It looks something like this: https://{cloud_storage_provider}/?secret_token={some_unique_token} All the security of this model relies in the randomness and length of the secret token.…
-
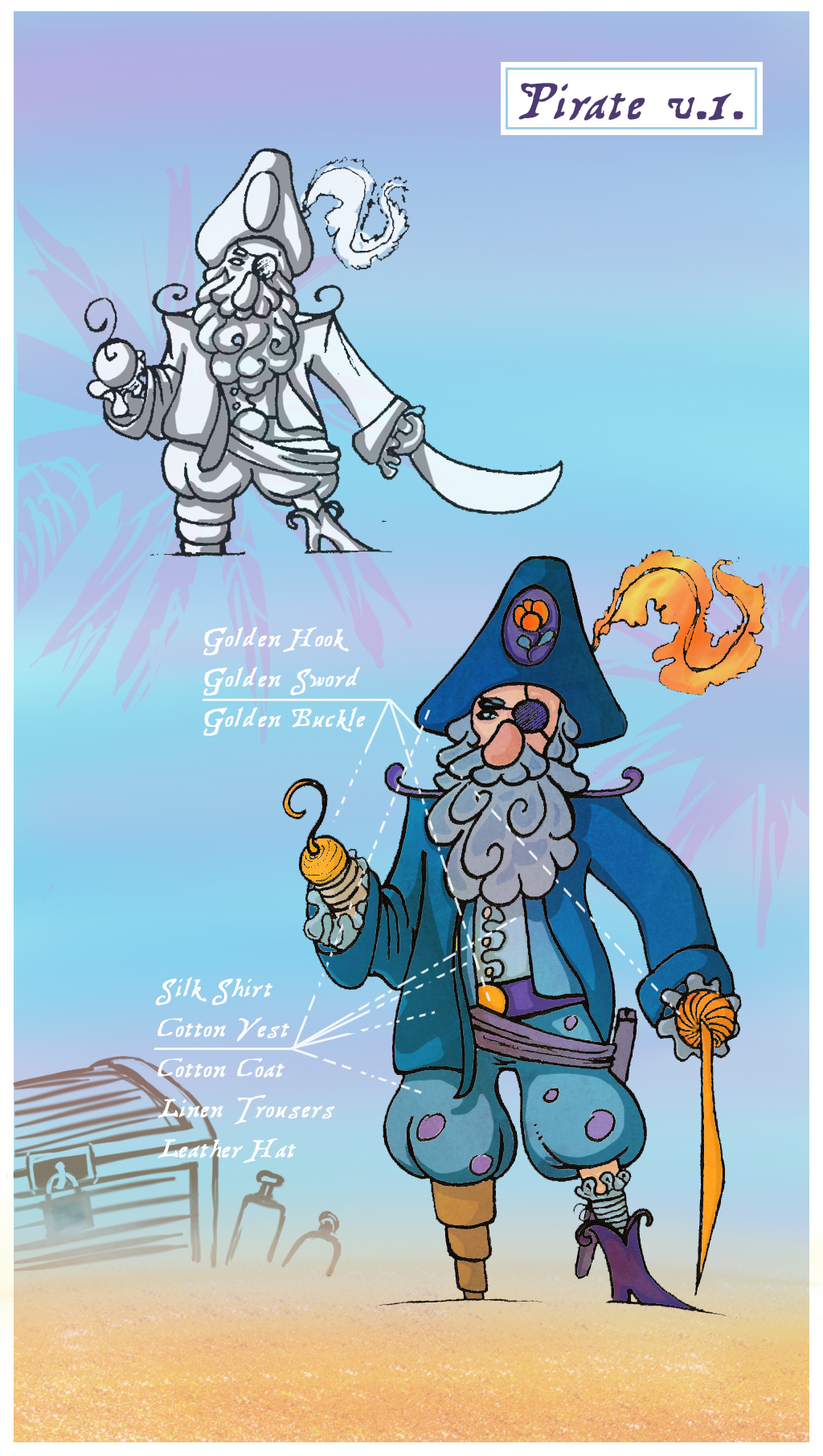
A slightly more complex 3D printing project – The Pirate
I bought a Prusa i3 kit some time ago, in an effort to experiment a little bit around 3D printing. In parallel, I had a discussion about everything with Dani (like most of our discussions). Things like Kickstarter, games, prototyping and USB sticks were predominant in that particular one. A few days later he came back…
-
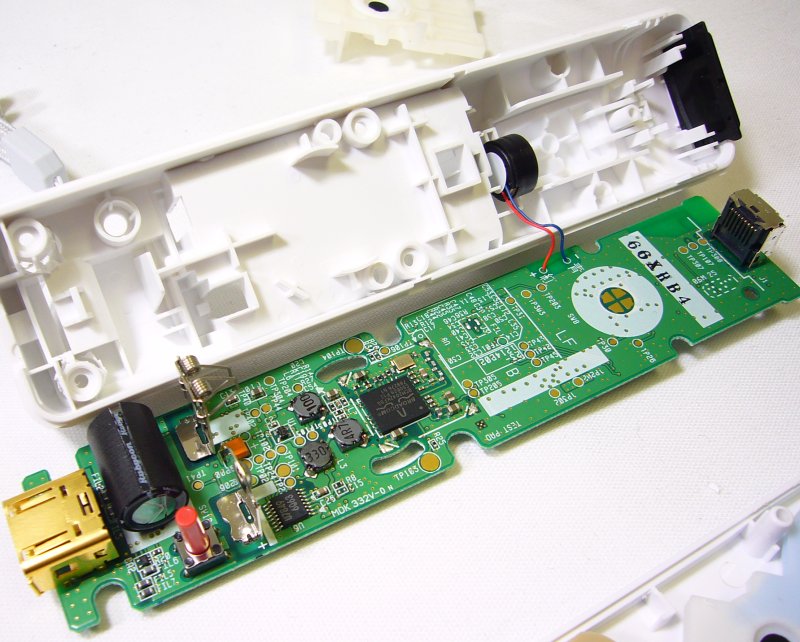
Hacking the Wii remote control
You know that sensation when you are ready to make that winning move but the Wii Remote is thinking otherwise and refuse to move as you intended? I feel the same and I had strong bad feelings about my controller(s). You might have noticed that I never considered that it might be my lack of skills, the…
-
Updating Kali Linux from behind a restrictive proxy
I installed Kali Linux from the mini ISO, so I ended up with a fully functioning Linux system but with little to no tools (just nmap and ncat). In order to install the tools that are making Kali what it is, I had to install the metapackages. For me, the easiest option was to install all of…
-
http vs https performance
A while ago I had a huge argument with a development team regarding the usage of https. Their major concern was that the impact on performance would be so big that their servers wouldn’t be able to handle the load. Their approach was to use https just for the login sequence and plain text communication…
-
Is application security an agile process?
No. Judging by the way it is marketed and sold today, application security is not, by any means, agile. Can it be? Well, Microsoft says so. When it comes to security, Microsoft changed a lot in the past decade. The development frameworks they offer have built-in security features nowadays. So, if they say security can be built…
-
WordPress Security Implementation Guideline
I (finally) managed to complete my project on WordPress Security. You can find it here: https://www.owasp.org/index.php/OWASP_Wordpress_Security_Implementation_Guideline I also delivered a presentation at the OWASP Romania InfoSec Conference 2014 on this topic. The presentation is on SlideShare: WordPress Security Implementation Guideline – Presentation for OWASP Romania Infosec Conference 2014 from Dan Vasile Yours truly in action:
-
Updating your Raspberry Pi
Once you’ve installed Raspbian on your Raspberry Pi, it’s time to upgrade the Pi and the OS. Four simple commands: # sudo apt-get install rpi-update # sudo rpi-update # sudo apt-get update # sudo apt-get upgrade
-
Installing Raspbian from scratch without a keyboard or a monitor
So, you got your Raspberry Pi, a nice SD card, but you can’t remember the last time you saw a keyboard and the only thing around you is a laptop with Windows. Don’t worry, there’s a simple solution. Download the latest version of Raspbian and Win32 Disk Imager. Start Win32 Disk Imager (“Run as Administrator”).…